Good practice, Part 7: Digital e-mail signatures

A digitally signed e-mail proves to the recipients that the message has not been edited in transit, and verifies the identity of the sender. So a digital signature enables trust and non-repudiation. It’s a good practice to sign e-mails. It’s as simple as that. But how do digital signatures actually work? Knowing that enables you to understand why you should trust and use them. This article will briefly explain that.
We must first understand the basics of asymmetric cryptography, digital certificates and hashes to get our heads around this topic.
Asymmetric cryptography
Asymmetric keys are in short, a key pair (private and public key) used in combination to encrypt and decrypt information. If something is encrypted using a private key, it is only possible to decrypt it using the corresponding public key. This also works the other way around. Something encrypted with a public key can only be decrypted using the corresponding private key. It is important to never disclose the private key to anyone. The public key on the other hand can be shared with anyone. It is not possible to recreate the private key from the public key.
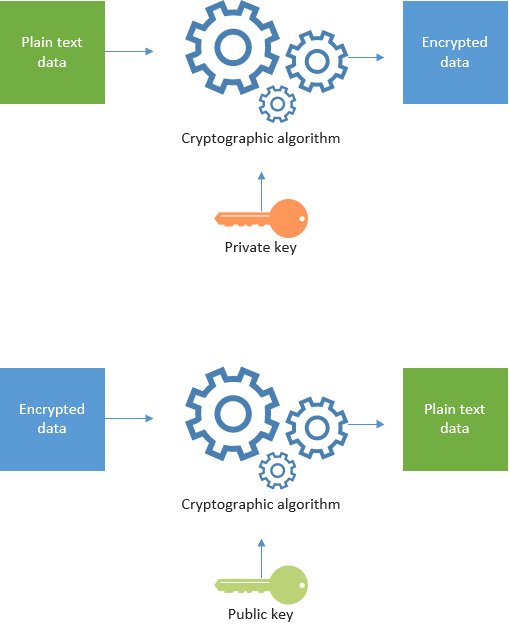
Digital certificate
A digital certificate is a digital document that verifies the ownership of a public key. It contains a public key, and information about the owner like name, address, e-mail address etc. Anyone can create a digital certificate, but a digital certificate is only as trustworthy as its creator. That is why we have certificate authorities (CA) like DigiCert. They are trusted by the vast majority of vendors like Microsoft. Any digital certificate issued by a major CA is therefore automatically trusted in their systems like e-mail clients. A CA becomes trusted only if they prove to carefully verify the information they vouch for. So before a CA agrees to sell you a digital certificate containing your phone number, they might call that number to verify you are actually the owner.
When you buy a digital certificate from a CA they will provide you with a asymmetric key pair and the digital certificate containing the public key from the key pair.
Hashes
A hash value (also known as digest) is the computed result after feeding data into a hash function. The hash function will always produce the same hash value as long as the data input is the same. On the other hand, the smallest change in the data input will result in a totally different hash value. Hash values are often used to verify data integrity.
Signing an e-mail
Lets say that you have obtained a digital certificate from a major CA, and imported it and the corresponding private key into your e-mail client. What now? Just tick the “Sign” option when composing a message and you are done. It’s that easy. But how does it work?
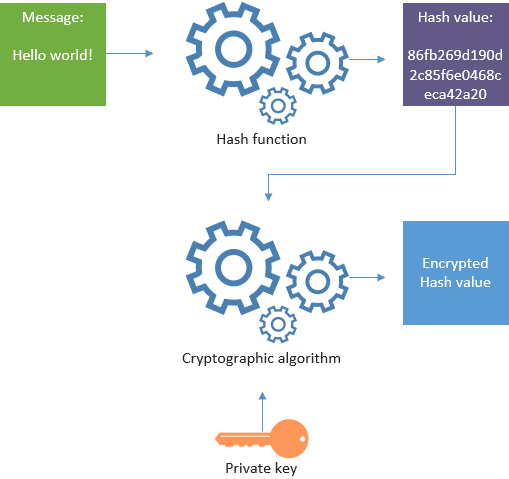
If you write a e-mail message and digitally sign it, a hash value is created from the e-mail message. The hash value is then encrypted with your private key.
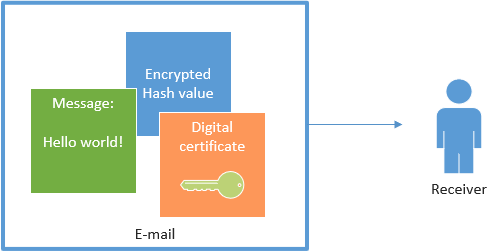
When you send the e-mail, the encrypted hash value is attached along with your digital certificate (which contains your public key, remember?).
When the receiver opens your e-mail they will then use the public key in your digital certificate to decrypt the hash value. If they are able to decrypt the hash value with your public key, they know you encrypted it using your private key.
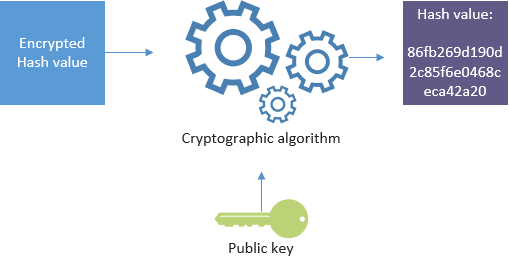
They now have your hash value of your e-mail, and they know you created that hash value. They can now create their own hash value of the message they received by feeding it into the same hash function you used.
If the hash value they created matches the hash value you sent them, they know for a fact that the message has not been edited in transit. And since you used a digital certificate from a trusted CA, they can also trust that the sender is actually you, and not an impostor.
